
Résumé
The attack was caught before it could inflict harm. On 8 February 2021, hackers remotely accessed the city of Oldsmar's water treatment plant in Florida and changed the level of sodium hydroxide by 111 times. At these levels, the 15,000 residents would have fallen seriously ill. Luckily, the water never reached their homes - the Florida water treatment hack was foiled.
Introduction
The attack was caught before it could inflict harm. On 8 February 2021, hackers remotely accessed the city of Oldsmar's water treatment plant in Florida and changed the level of sodium hydroxide by 111 times. At these levels, the 15,000 residents would have fallen seriously ill. Luckily, the water never reached their homes - the Florida water treatment hack was foiled. 1
|
|
Download the article here |
More recently - on 9 May 2021 - a hacker group called Darkside, launched a ransomware attack, which shut down an essential US energy pipeline.
The Colonial Pipeline transports 2.5 million barrels of refined petroleum products from the US Gulf Coast to major US cities on the East Coast. 2 The disruption led to panic buying at US gas stations and threatened to cause significant economic damage. It is reported that the organisation had to pay a USD 5 million ransom to receive a key to recover data that have been encrypted by the hacker group. 3
Just 3 days later, the same hacker group attacked the North American division of German chemical distributor, Brenntag, resulting in ransom pay out amounting to c. USD 4.4 million, as a part of the group’s campaign targeting critical industries in North America. 4
These are just a few examples of the gravity and severity of cyberattacks.
To put this into context, Varonis.com reports that hackers attack on average every 39 seconds, which equates to 2,244 times a day. 5

Hackers attack on average every 39 s, which equates to 2,244 times a day
Many companies are often unaware that they have been attacked, while others choose not to disclose these events due to fear of reputational damage. 6 The frequency and magnitude of these attacks is only set to increase as our world becomes even more digitally connected.
Let us go through a few of the threats that companies face.
Threat 1: Lack of sufficient cybersecurity capabilities
At the start of the pandemic, companies were forced to send their workforce home and their IT infrastructure was stretched beyond imagination.
It presented the perfect opportunity for cyberattackers to strike.

The highest reported ransomware pay out amounted to in excess of
USD 4.5m
The videoconferencing tools that employees started to use to communicate were particularly vulnerable. According to Deloitte, nearly half a million workers had their personal data stolen from cyber weaknesses caused by videoconferencing software during the first lockdown. 7
Ransomware attacks, identity fraud and phishing campaigns all rose significantly during this period. Brute force attacks which used password cracking tools and account checking tactics were also used frequently to log into online accounts. Bank fraud and identity theft also became widespread.
According to IBM, the average cost of each data breach that a company experienced in 2020 was USD 3.86 million. Statistically, it took on average 207 days to identify a breach, while it took an average of 280 days from the point the breach was identified until it was fully contained. 8
Ransomware, an extortion software that encrypts your data demanding a ransom for its release (Kaspersky) and the fastest growing malware according to the US Department of Justice, reportedly starts to encrypt the victim’s files in only 3 seconds. 9 Moreover, the highest reported ransomware pay out amounted to in excess of USD 4.5 million. 10 Such calibre of crime leaves people and organisations damaged and powerless.
Threat 2: The exponential growth in data
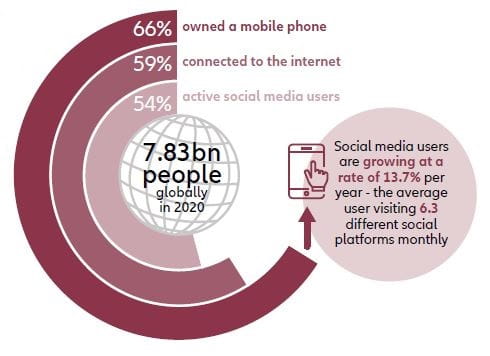
Cybercrime is likely to rise considerably even after the pandemic. The exponential growth in insufficiently secured data in the digital world that we are entering is prone to be a major factor.
As of 2020, there were 7.83 billion people living on Earth. 66% owned a mobile phone. Meanwhile 59% were connected to the internet.
54% were also active social media users 11
These figures have since increased tail-winded by the pandemic. According to DatarePortal.com, globally, social media users are growing at a rate of 13.7% per year, with the average social media user visiting or using 6.3 different social platforms every month 12
The huge amounts of data that we are now creating presents even greater opportunities for cybercriminals to attack. However, this is nothing compared to what we might experience with the emergence of 5G.
Threat 3: Growing internet connectivity
When 5G fully arrives, there will be an explosion of devices connected to the internet producing even larger quantities of data.
By 2025, it is expected that there will be more than 30 billion connected devices, which equates to 4 devices per person globally. 13
It's not just smartphones, laptops and computers that will be connected to 5G – we will also see a growing number of autonomously driven cars, devices inside smart homes, and industrial equipment in factories, which will contain 5G chipsets.

Better security is the solution
Cybersecurity will be an increasingly crucial component in our emerging technological economy.
The global cybersecurity market is expected to grow at a rate of 12.6% per annum until 2030, rising from USD 119.9 billion in 2019 (before Covid-19) to USD 433.6 billion by 2030. 14
In fact, according to a recent report from Accenture Security, more than 20% of IT budgets are being spent by leading companies on advanced technology, which is almost double what has been spent in the last three years. 15

How to leverage the growth in cybersecurity?
Cybersecurity is a complex industry targeting a variety of issues, while providing a great opportunity for diversification and direct exposure.
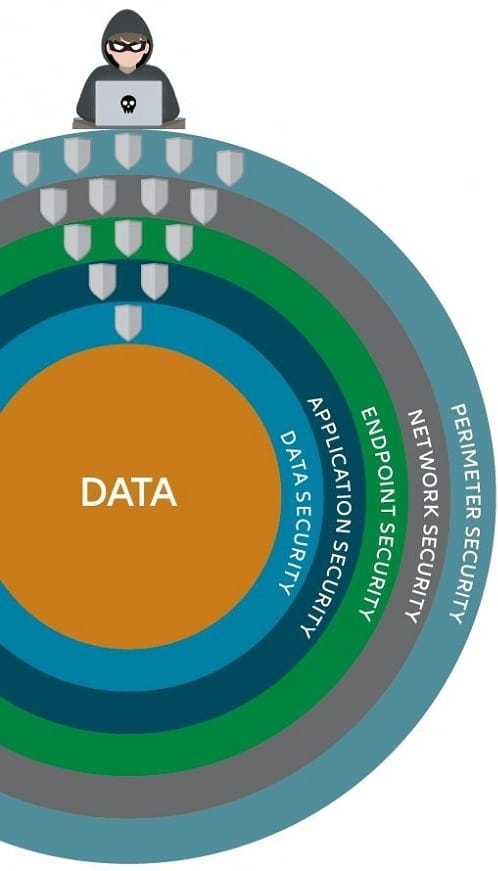
For instance, perimeter security is probably the most relevant to an individual’s daily activities. This includes the firewall in your browser, but also security isolation systems that recognise threats to a computer network. Cisco Systems* is one of the most well-known companies that operate in this space.
Network security has become particularly significant during the pandemic when there was a huge increase in workers logging in remotely. But this will not stop after the pandemic has passed. Cloud computing is set to see this trend continue in the future and companies will be required to cope with a hybrid structure of internal and external networks. Companies, like FireEye*, now help firm improve this type of security.
There is also endpoint security, which aims to protect computer networks from devices such as desktops, laptops and smartphones that are connected to it.
This can be an area of vulnerability for computer networks and has become increasingly important as more-and-more companies embrace cloud technology. A company that works in this space is CrowdStrike*, which helps ensure endpoint security and provides threat intelligence for the companies it works for.
Application security is also important and represents the intellectual property of many firms.
Companies will need to protect data and the code used to make applications they own, which companies like Zscaler* can help them do.
Finally, there is data security itself. In other words, protecting digital data, such as those stored in databases from cyberattacks. Gartner estimates that this market will grow from USD 9.8 billion in 2019 to circa USD 14.0 billion by 2024. 14
A good example of a company that operates in this space is Okta*. It provides companies with a platform that can help secure the identity of customers and workers.
What’s next?
Cybercrime is a long-term trend that sped up tremendously as a result of the pandemic.
This has, in turn, cemented cybersecurity’s importance as part of the global economy going forward.
The increasing sophistication of cybercrime is alarming and difficult for most ordinary people to comprehend. According to IBM Security's X-Force “35% of investigated incidents leverage [their target’s] vulnerabilities in the attack”. 16
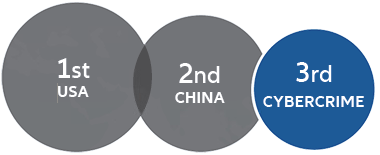
It is a serious issue. If the costs of cybercrime in 2021 were the GDP of the country, it would be the third largest in the world after the US and China. Cybercrime is expected to cost victims USD 6 trillion in 2021. 17
There is no one-size-fits-all solution
Companies will require different layers of cybersecurity that are unique to them. In some instances, coverage of every layer of cybersecurity will be required from various suppliers. This is why it is absolutely crucial to have a strong cybersecurity industry. Without this type of infrastructure, it will be impossible for a future digital economy to emerge.
This is an industry that is likely to see significant growth in the future. That is why the time to invest in cybersecurity is now.
References:
1 Robles, F., & Perlroth, N. (2021, February 9). ‘Dangerous Stuff’: Hackers Tried to Poison Water Supply of Florida Town
https://NYtimes.com/2021/02/08/us/oldsmar-florida-water-supply-hack.html
2 Colonial Pipeline: cyberattack draws attention to besieged US energy system (2021, May 11)
https://FT.com/content/de0be95e-fbd4-40ff-ab3a-2e8490fdcd32
3 Javers, E. (2021, May 14). Colonial Pipeline paid $5 million ransom to hackers
https://CNBC.com/2021/05/13/colonial-pipeline-paid-ransom-to-hackers-source-says.html
4 https://WashingtonPost.com/politics/2021/05/14/cybersecurity-202-biden-says-russian-government-was-not-involved-with-colonial-pipeline-hack
5 https://eng.umd.edu/news/story/study-hackers-attack-every-39-seconds University of Maryland 2007
6 https://ITgovernance.co.uk/blog/data-breaches-and-cyber-attacks-quarterly-review-q1-2021
7 Nabe, C. (2020, December 15). Impact of COVID-19 on Cybersecurity. Deloitte Switzerland
https://Deloitte.com/ch/en/pages/risk/articles/impact-covid-cybersecurity.html
8 IBM Security. (2020). Cost of a Data Breach Report 2020 https://Capita.com/sites/g/files/nginej291/files/2020-08/Ponemon-Global-Cost-of-Data-Breach-Study-2020.PDF
9 https://Justice.gov/criminal-ccips/file/872771/download
10 https://ITgovernance.co.uk/blog/the-5-biggest-ransomware-pay-outs-of-all-time
11 https://DatarePortal.com/global-digital-overview (April 2021)
12 Kemp, S. (2021, April 19). Digital 2021: Global Overview Report. DataReportal – Global Digital Insights https://datareportal.com/reports/digital-2021-global-overview-report
13 Kenworthy, R. (2019, November 18). The 5G And IoT Revolution Is Coming: Here’s What To Expect
https://Forbes.com/sites/forbestechcouncil/2019/11/18/the-5g-iot-revolution-is-coming-heres-what-to-expect
14 ResearchAndMarkets.com (2020, November 19)
https://BusinessWire.com/news/home/20201119005835/en/Global-Cyber-Security-Market-2020-to-2030---by-Component-Security-Type-Deployment-Enterprise-Use-Case-and-Industry---ResearchAndMarkets.com
15 Accenture Security. (2020). tate of Cybersecurity Report 2020 https://Accenture.com/_acnmedia/PDF-116/Accenture-Cybersecurity-Report-2020.pdf
16 Firch, J. M. (2021, May 17). 10 Cybersecurity Trends You Can’t Ignore In 2021 https://PurpleSec.US/cyber-security-trends-2021/
17 Morgan, S. (2021, April 27). Cybercrime To Cost The World $10.5 Trillion Annually By 2025 https://CyberSecurityVentures.com/hackerpocalypse-cybercrime-report-2016/
Important information:
* This is no recommendation or solicitation to buy or sell any particular security. A security mentioned as example above will not necessarily be comprised in the portfolio by the time this document is disclosed or at any other subsequent date.
Investing involves risk. The value of an investment and the income from it may fall as well as rise and investors might not get back the full amount invested.
Allianz Cyber Security is a sub-fund of Allianz Global Investors Fund SICAV, an open-ended investment company with variable share capital organised under the laws of Luxembourg. The value of the units/shares which belong to the Unit/Share Classes of the Sub-Fund that are denominated in the base currency may be subject to a strongly increased volatility.
The volatility of other Unit/Share Classes may be different. Past performance is not a reliable indicator of future results. If the currency in which the past performance is displayed differs from the currency of the country in which the investor resides, then the investor should be aware that due to the exchange rate fluctuations the performance shown may be higher or lower if converted into the investor’s local currency.
This is for information only and not to be construed as a solicitation or an invitation to make an offer, to conclude a contract, or to buy or sell any securities.
The products or securities described herein may not be available for sale in all jurisdictions or to certain categories of investors.
This is for distribution only as permitted by applicable law and in particular not available to residents and/or nationals of the USA. The investment opportunities described herein do not take into account the specific investment objectives, financial situation, knowledge, experience or specific needs of any particular person and are not guaranteed.
The views and opinions expressed herein, which are subject to change without notice, are those of the issuer companies at the time of publication.
The data used is derived from various sources, and assumed to be correct and reliable at the time of publication. The conditions of any underlying offer or contract that may have been, or will be, made or concluded, shall prevail.
The duplication, publication, or transmission of the contents, irrespective of the form, is not permitted; except for the case of explicit permission by Allianz Global Investors GmbH.
For investors in Europe (excluding Switzerland)
For a free copy of the sales prospectus, incorporation documents, daily fund prices, key investor information, latest annual and semi-annual financial reports, contact the management company Allianz Global Investors GmbH in the fund’s country of domicile, Luxembourg, or the issuer at the address indicated below or (Regulatory.AllianzGI.com).
Austrian investors may also contact the Austrian information agent Allianz Investmentbank AG, Hietzinger Kai 101-105, A-1130 Vienna.
Please read these documents, which are solely binding, carefully before investing.
This is a marketing communication issued by Allianz Global Investors GmbH (AllianzGI.com) an investment company with limited liability, incorporated in Germany, with its registered office at Bockenheimer Landstrasse 42-44, 60323 Frankfurt/M, registered with the local court Frankfurt/M under HRB 9340, authorised by Bundesanstalt für Finanz¬dienstleistungsaufsicht (BaFin.de).
Allianz Global Investors GmbH has established branches in the United Kingdom, France, Italy, Spain, Luxembourg, Sweden, Belgium and the Netherlands.
Contact details and information on the local regulation are available here (AllianzGI.com/Info).
For investors in Switzerland
For a free copy of the sales prospectus, incorporation documents, daily fund prices, key investor information, latest annual and semi-annual financial reports, contact the management company Allianz Global Investors GmbH in the fund’s country of domicile, Luxembourg, the Swiss funds’ representative and paying agent BNP Paribas Securities Services, Paris, Zurich branch, Selnaustrasse 16, CH-8002 Zürich or the editor either electronically or by mail at the given address or (Regulatory.AllianzGI.com).
Please read these documents, which are solely binding, carefully before investing. This is a marketing communication issued by Allianz Global Investors (Schweiz) AG, a 100% subsidiary of Allianz Global Investors GmbH.
AdMaster: 1661629

Résumé
One might think that in the US, the issue of water infrastructure should not be an extraordinary problem. But this is not the case. Some water pipes are a hundred years old, dams are dangerous and lead pipes are a concern for politicians and citizens alike. The resulting investment pressure is immense. Yet the US is only one example of the global need to expand or improve water infrastructure. Read more about the opportunities and risks of the US water infrastructure and its importance for investors in our analysis.







